The following instructions are applicable to SOS 2010 and later. Earlier versions of SOS require slightly different command lines. See: http://www.sosoft.com/fod/doc430-startingdbasservice.pdf
Overview
The primary reason to configure the SOS SQL Anywhere database to run as a service is that it will continue to run even if nobody is logged into the server computer. Assuming that you set the service to run automatically, it will start as soon as the server boots up. When a service starts, it uses a special system account called LocalSystem (or use another account you specify). The service is not tied to the user ID of the person starting it, and therefore is not stopped when that person logs off.
To add a new service
- On the computer that runs the SOS database, open a command prompt.
- NOTE: This must be an “administrator mode” command window, so in Server 2008, Vista, and other recent versions of Windows, be sure to right-click the Command Prompt icon and select “Run as Administrator”. In previous versions, it will be enough to log into Windows using an account that has administrator privileges.
- Change to the C:\SOS\SA\Bin32 directory (that is, the SA\Bin32 folder within the folder containing your SOS program files, assuming a default installation on the C: drive).
- Execute the Service Creation Utility using the -w option. For example, to create a database server service called “mysos”, which starts the specified engine with the specified parameters type the following command, all on one line. The options below will set the service to run under the system account, as a network service, to start automatically, to display the database icon in the system tray, and to be named “mysos”. It will appear in the Windows Services Manager as “SQL Anywhere – mysos”. If you are running the database in 64-bit Windows, using the 64-bit option is recommended, but either version of the engine will work. The 64-bit engine often provides better performance, especially for larger databases. Note that the -i option to display the icon in the system tray won’t work on Vista, 7, or Server 2008 and later, so omit that option if using one of those. Service configuration commands are case sensitive. Type your options exactly as shown (eg: “automatic” will fail but “Automatic” will work).
32-bit Windows:
dbsvc -as -t network -s Automatic -i -w mysos c:\sos\sa\bin32\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
64-bit Windows:
dbsvc -as -t network -s Automatic -i -w mysos c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
- After executing the command, you will find a new Windows service listed in Windows’ Administrative Tools > Services applet: SQL Anywhere – mysos. You can adjust the properties for the service just as you would for any other service.
Notes on adding a service:
- Service names must be unique within the first eight characters.
- If you choose to start a service automatically, it starts whenever the computer starts Windows.
- Choose the account under which the service will run: the special LocalSystem account or another user ID.
- If you want the service to be accessible from the Windows desktop, check Allow Service to Interact with Desktop. If this option is cleared, no icon or window appears on the desktop or use the -i option when creating the service.
Removing a service
Removing a service removes the server name from the list of services. Removing a service does not remove any software from your hard disk. If you wish to re-install a service you previously removed, you need to re-type the options.
To remove a service (Command line)
- Open an administrator command prompt. (See NOTE under item 1 in the first section of this document.)
- Execute the Service Creation utility using the -d option. For example, to delete the service called “mysos”, without prompting for confirmation, type the following command:
dbsvc -y -d mysos
Notes on removing a service:
In some cases “deleting” a service just marks it for actual removal when you next reboot the system. If you want to delete a service in order to add a new one with the same name, you will have to reboot after doing the deletion, then add the new service when the system has restarted. If you use a different name for the new service, you can disable the old one using the Windows services applet, then delete it as described above so that it will be removed the next time you reboot. You can then add the new service and start it, as long as you are careful to use a different name.
Detailed Reference for the DBSVC Utility
(see also page 820 in the SQL Anywhere Database Administration manual)
Managing services using the dbsvc command-line utility
Syntax dbsvc [ options ] <svc>
dbsvc [-q] [-y] -d <svc>
dbsvc [-q] -g <svc>
dbsvc [-q] -l
dbsvc [-q] [-y] <creation options> -w <svc> <details>
| Option |
Description |
| -a |
Account name to use (used with -p) |
| -as |
Use local system account |
| -d <service name> |
Delete a service |
| -i |
Allow service to interact with the desktop. Displays an icon that you can double-click to display the database server messages window. |
| -g <service name> |
Get details of a service |
| -l |
List all SQL Anywhere services |
| -p |
Password for account (used with -a) |
| -q |
Do not print banner |
| -rg dependency… |
Specify group dependencies when creating a service |
| -rs dependency… |
Specify service dependencies when creating a service |
| -s startup |
Startup option (default is manual). You must specify Automatic, Manual, or Disabled. |
| -sd <description> |
Use this option to provide a description of the service. The description appears in the Windows Service Manager. |
| -t <type> |
Type of service, eg: Network |
| -u <service name> |
Starts the service named service_name |
| -w <executable parameters> |
Creates a new service, or overwrites one if one of the same name exists. If you supply -y, the existing service is overwritten without confirmation. |
| -x <service name> |
Stops the service named service_name |
| -y |
Delete or overwrite service without confirmation |
A service runs a database server or other application with a set of options. This utility provides a comprehensive way of managing Adaptive Server Anywhere services on Windows. The Service Creation utility provides the same functionality as the Service Creation wizard in Sybase Central.
You must be a member of the Administrators group on the local machine to use the Service Creation utility.
Exit codes are 0 (success) or non-zero (failure).
This utility accepts @filename parameters.
Examples
(all executed from the c:\sos\sa\win32 command prompt, even if creating a 64-bit service)
Create a personal (not networked) database service called mypersonaldb, which starts the specified standalone engine with the specified parameters. The engine runs as the LocalSystem user:
32-bit:
dbsvc -as -w mypersonaldb c:\sos\sa\bin32\dbeng11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
64-bit:
dbsvc -as -w mypersonaldb c:\sos\sa\bin64\dbeng11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
Create a network database service called mynetdb. The server runs under the local account, and starts automatically when the machine is booted (all on one line):
32-bit:
dbsvc -as -s Automatic -t Network -w mynetdb c:\sos\sa\bin32\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
64-bit:
dbsvc -as -s Automatic -t Network -w mynetdb c:\sos\sa\bin32\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
List all details about service myserv:
dbsvc -g myserv
Delete the service called myserv, without prompting for confirmation:
dbsvc -y -d myserv
How-To Easily Determine Which Date-of-Service is Outstanding on a Patient Account
SOS Product: Office Manager for Windows
Introduction
You may get a call from a client wanting to know which dates of service are still outstanding on his/her account as well as how much is outsanding on each date. easisert way to tell is to bring up the By-Charge Ledger for the client.
Here’s the process:
- Go to the Active Patient List
- Highlight the client, then click on the Ledger icon (Little Book.) located at ?
- Click the ledger by charge icon (Dollar Sign.)
- If the view is not collapsed, click on the Collapse All icon (3 to 1 square.) This will show only the charges. Any charges in black are fully paid and anything in red has an outstanding balance.
- If you need to know which payers have a balance, click on the plus sign (+) in front of the date-of-service and it will show you which payers have an outstanding balance and how much.
Conclusion:
While you are on the phone or the client is at the window, the data is quickly accessed and it will save you time.
Whenever a user initiates an action that asserts an exclusive lock on a table, or even a single row in a table, it will cause other users trying to change or save data to the locked table or row to be “blocked” — forced to wait until the first user concludes the action. While blocked, users will experience an ongoing “hourglass” or spinning circle icon. Often that condition will be misinterpreted as a program crash. To determine if there is a locking/blocking situation, the administrator can run a simple query in DBISQL while the blocking is still on-going to show the condition of the user connections.
SOS has worked hard to prevent locks that last more than a split-second, but even with mature software like SOS, it is possible that something slipped through. If you are able to identify a persistent locking situation, be sure to report it as soon as you can.
After opening DBISQL and logging in with a SUPER level account, execute the following query:
SELECT number, userid, blockedon, lockrowid, locktable FROM sa_conn_info()
The results will look something like the figure below:

We have highlighted the row that shows the user connection that is being blocked. The “blockedon” column value is the number of the connection that is responsible for the block. Matching that number to the row with the same value in the “number” column tells us that it is the user SUPER who is creating the lock that is blocking the highlighted user. Other columns in the highlighted row show us the id of the specific row that is locked, as well as the name of the database table in which that row is found. Until this lock is released, the blocked user “OM_MF” will not be able to proceed.
In practice, the user setting the lock will generally be in the form <module-prefix>_<UserID>. For example, “SC_MF” would indicate user MF connecting from module Scheduler (SC). Other prefixes are OM for Office Manager, CM for Case Manager, and AD for the Admin module. In our example above, we used DBISQL to create the lock, which is why there is no prefix.
Once you know the UserID of the responsible user, ask the user to complete the operation, return to the indicated module’s main menu, or exit that module altogether. Doing so will immediately remove the lock, and any blocked users will return to normal operation.
If you should repeatedly run into a scenario the you can identify and reproduce, please report your findings to SOS tech support as soon as possible, so that our developers can diagnose the problem and roll out a fix.
TPM is a chip that is included on higher end business-oriented computers. If present, it is used by BitLocker.
If you don’t have TPM in your computer, you can still use BitLocker if you follow the steps below (from a post on answers.microsoft.com ).
How to Configure Computer to Enable BitLocker without Compatible TPM:
Administrators must follow the steps below to configure their Windows 8 computers to allow enabling Bit Locker Drive Encryption without compatible TPM:
a. Log on to Windows 10 computer with an account that has administrative privileges.
b. Assuming that the computer has been configured to display the classic start menu, click Start (or the Windows icon) and at the bottom of the menu in search box type GPEDIT.MSC command and press enter key.
c. On the opened Local Group Policy Editor snap-in, from the left pane expand Computer Configuration > Administrative Templates > Windows Components > Bit Locker Drive Encryption and from the expanded list click to select Operating System Drives.
d. From the right pane double-click “Require additional authentication” at startup.
e. On the opened box click to select Enabled radio button and ensure that under Options section Allow Bit Locker without a compatible TPM checkbox is checked.
f. Once done, click Ok button to allow the changes to take effect and close Local Group Policy Editor snap-in.
SOS users are often reminded of the importance of disk encryption to keep their precious data safe in the event of computer loss or theft. For many years we have been recommending use of TrueCrypt, which now has been re-born as VeraCrypt, or Microsoft’s BitLocker feature (Available in Pro and Enterprise versions of Windows).
Here’s an article that explains how to upgrade from Windows 10 Home to Windows 10 Pro.
For those using non-commercial versions of Windows such as Windows Home, VeraCrypt is a free, proven, reliable, and effective option, and full disk encryption is recommended. There can be a hitch, however. At present You can only encrypt the boot (main) drive in your computer if it is partitioned with the older MBR method. There are several YouTube videos and articles on the web that show various techniques that can be used to convert a drive from GPT to MBR, after which you can use all the features of VeraCrypt. It is possible to lose ALL your data converting from GPT to MBR, so it is ESSENTIAL that you back up your entire C drive before proceeding with any of those tools. If your drive is partitioned as GPT, GUID, UEFI, or EFI, and you are not technically oriented, you might be better off just upgrading Windows to the Pro version and using Microsoft’s BitLocker feature.
Related:
How to enable BitLocker even if your computer does not have TPM
Overview
By default, the SOS database is not encrypted, though the physical layout of the database files is such that assembling a coherent record of data would be difficult. Nonetheless, inspection of the database files could reveal identifying information, so some level of encryption is recommended in most all situations, and always if the database is transported from place to place on a portable computer or on removable media (such as removable disk, CD, DVD, USB memory key, or tape) or if the database is transmitted from one location to another electronically.
You may choose to protect the data in the database by selecting either “simple encryption” or “strong encryption” (AES, Advanced Encryption Standard).
Simple Database Encryption
Simple encryption is equivalent to obfuscation and prevents someone using a disk utility, text editor, or even a word processor from being able to read patient names or other information stored in the database files. Simple encryption uses a built-in key and therefore does not require the user to provide a key to encrypt the database. Once encrypted, the information can still be accessed using the SOS and Sybase programs exactly as with an unencrypted database. In addition, utilities such as DBTRAN (which translates the transaction log into readable text) can still be used by anyone who knows how, without the need to provide a password or encryption key. It is therefore essential to secure the computer and drive on which the transaction log (SOSDATA.LOG) is stored, even if using simple encryption. The folder(s) in which the database and log files are stored should NEVER be shared across a network for this reason. Windows shares are entirely unnecessary for use of the SOS system, and for the reasons just given, undercut efforts to keep your data secure.
Strong Database Encryption
Implementing strong encryption is a more complex procedure but renders the database completely inaccessible without an encryption key. There is no back door or recovery possible if the encryption key value is lost or forgotten, so if no reliable key management system is possible in your organization, you should think twice about it.
Changing the Encryption Level of an Existing Database
In order to change the encryption level of your database, you must rebuild it. Starting with Release 2007.02 (December, 2007 build), the SOS Database Rebuild Utility may be used to encrypt your database with Simple Encryption. There is no automated option for applying strong encryption, though SOS tech support can provide you with hands-on assistance to go through the steps, specifically:
- Backup your current database.
- Unload your database to a set of ASCII tables.
- Initialize a new encrypted database.
Reload the new database with the previously unloaded data.
| Encryption Option |
Advantages |
Disadvantages |
|---|
| No encryption |
No rebuild required. Best performance. Best chance of database recovery in the event of corruption. No encryption key to remember or safeguard. |
Patient information – such as names – can be read by opening the database files with a text editor or word processor. Unless physical access to the database is carefully restricted, this option could constitute a HIPAA violation. This option is not supported by the Rebuild Utility. |
| Simple encryption |
No encryption key to remember or safeguard. Minimal performance or database recovery impact. Obscures data in database files, preventing it from being accessed by unsophisticated methods. Easy procedure to implement. No configuration changes needed in database startup. |
Does not provide any encryption of the database log (the sosdata.log) file, which can be translated to readable text using a Sybase utility. Any user can still start the database, and once it is started, can access data as long as he or she has an SOS password that permits access. |
| Strong encryption (recommended, but requires a short consultation with SOS tech support to enable) |
Very strong AES 128 bit or even stronger AES 256 bit data protection. Your database and log cannot be started or accessed without the encryption key that you have created. |
Somewhat more difficult, manual process to implement. Configuration changes necessary for database startup. File containing the encryption key must be secured somewhere on the network or the encryption key must be typed in to start database. Most importantly, loss of your encryption key will render your database useless. Finally, use of strong encryption will incur a performance penalty, in all likelihood in the range of two to five percent, though there are many variables in play. |
When selecting the Strong Encryption option, you must provide an encryption key, which is a string of characters that will be used to encrypt and decrypt the contents of your database and transaction log. The normal rules for password generation apply:
- Use no fewer than 8 characters. SOS’s SQL Anywhere database supports keys of up to 60 characters. A length of 10 to 30 is recommended. Longer keys are more difficult to crack, but theoretically could result in slower performance. The better your hardware, the less likely you would be able to detect a difference.
- Include upper and lower case letters, plus numbers and special characters in your encryption key. The key may contain any characters on your keyboard except <space>, semi-colon, apostrophe, and quotation mark characters.
- Strong keys are really random – no pet names or birth dates! Many free and low cost password generators are available to assist in generating random sequences of characters for use as passwords and encryption keys. Popular password managers such as LastPass and Roboform also include password generation tools.
Whenever you select or change your SOS database encryption password, we STRONGLY recommend that you use a key management system of some sort. There is no way to start or recover your database without it, so having a backup copy of your key in a secure location, available to all staff who might need it is mandatory to assure that you will not lose your data because of a forgotten key. Consider that you might not always be around to provide the key if it is ever needed, so appropriate recovery safeguards must be in place that do not depend on one person.
Performance Considerations Related to Database Encryption
There is a performance penalty for the use of encryption. The penalty is insignificant for the simple encryption method, but may be detectable when using strong encryption. If implementing strong encryption, the customer should pay even more attention to the selection of server hardware, choosing faster processors and disk systems, and, especially, more RAM than might otherwise be necessary. If the amount of RAM is sufficient to permit the entire database to be cached, the performance penalty should diminish and become relatively small after a period of active use. Note also that the length of the encryption key is related to performance, so if you are using a very long key and have performance issues, you can try rebuilding the database with a shorter key.
Recommendations
Given that the Simple Encryption option has minimal performance impact and provides some protection from unauthorized access, it is the minimum SOS recommendation. If your database is carried out of the office on a laptop or in unencrypted backups (such as a straight copy of the DATA folder onto an unencrypted flash drive or DVD), then serious consideration should be given to using Strong Encryption. In that case, it is essential that you carefully think through the entire process. Precautions must be taken to assure that only the most trusted employees are able to log into the server to encrypt the database. Again, however, keep in mind that losing the only employee who knows the encryption key could be disastrous and your plans must include assuring that you will not be left without a way to start and access your database.
How To Implement Simple Database Encryption
The easiest, and SOS recommended, way to change from no encryption to simple encryption is simply to use the Database Rebuild Utility, which will automatically apply simple encryption. It can be run from the command prompt, or using a menu item in the Administration module. This utility is named DBRBLD.EXE and is located in the SOS folder of the database server, or standalone computer if not running on a network. Within the Administration Module, navigate to “Database Tools” then “Database Rebuild Utility” as described below.
- Have all users exit all SOS programs.
- Backup your database as you normally do.
- On the computer where the database is located start SOSLogin.
- Enter an account ID and password of a user with SOS security administrator privileges.
- Click the “Admin” icon (the keys).
- Select Database Tools.
- On the list of utilities, select and run “Database Rebuild Utility”
How To Implement Strong Database Encryption
As mentioned previously, applying strong encryption is a manual process that involves several steps and some guidance from SOS tech support. The procedure includes the following steps:
- Backup your current database.
- Unload your database to a set of ASCII tables.
- Initialize a new encrypted database.
- Reload the new database with the previously unloaded data.
- Create and securely locate an option2.prm file containing an obfuscated version of your encryption key.
- Reconfigure the command line needed to start the encrypted database (see next section).
Before walking you through the procedure, SOS’s support tech will review with you the fact that loss of your encryption key will mean permanent loss of your data. The support tech also will ask you about your strategy to prevent loss of your database encryption key.
Starting a Strongly Encrypted Database
Once the database has been encrypted, whenever the database is started, the encryption key must be provided on the command line when the database is started, or the database engine must be instructed to prompt for the encryption key as it starts the database.
By default, SOS includes database engine startup parameters in a file in the SOS folder called SERVER.PRM. This file contains options for the database engine, which could, potentially run more than one database at a time. Options for each database run by the engine cannot be added to the engine options file. They must be placed after each database file on the startup command line. The following examples assume the database is running in a 64 bit Windows environment. If you are running 32 bit Windows, then replace “bin64” with “bin32” in the command line. All the following examples would be on a single line:
Default command line (simple or no encryption options):
c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db
Command line to prompt the user for the encryption key (-ep) every time the database is started:
c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db -ep
Command line with encryption key specified explicity:
c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db -ek secretkey
The last option is obviously less than ideal because the encryption key appears in plain text in the startup line invoked by your shortcut, batch file, etc. There is, however, an alternative. That part of the command line can be hidden using a provided utility that will hide the text from all but expert snoopers. When you select the Strong Encryption option during the rebuild, your encryption key will automatically be saved in an unreadable file called OPTION2.PRM, which you will find in the SOS folder as well as the DATA folder. You can therefore use this variation of the command above (entire command is typed on a single line):
c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db @c:\sos\option2.prm
If you wanted to create the unreadable option2.prm file manually, here is how it would be done:
1. Create a plain text file using Notepad or another text editor.
2. Enter -ek and the encryption key with which your database was encrypted.
3. Save the file as TEMP.TMP in your SOS folder.
4. Now apply simple encryption to the file, saving the encrypted copy as OPTION2.PRM with the command:
c:\sos\sa\bin64\dbfhide temp.tmp option2.prm
5. You will now have the original TEMP.TMP and an encrypted version called OPTION2.PRM in your SOS folder. Remember, if you lose your encryption key, there is no way to decrypt or run your database! Once you are sure that the encryption key value is safely recorded in case you should ever need it, delete the TEMP.TMP file. Hold down the shift key while deleting to be sure the file is deleted instead of just being moved to the recycle folder. If you have a utility for secure deletion of files, that would be even better. Now you can start the database using the following command, which does not expose the key:
c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db @option2.prm
A strongly encrypted database cannot be opened without its matching encryption key. For that reason it is essential that you either backup the option2.prm file containing your key, or securely record the key in a secure log, or formal key management system, that will document changes in the key over time. If you ever have to restore your data from an old backup, you will need the key that was in use when that database was backed up.
Including Your Encryption Key in the ODBC Configuration
In standalone installations, the database is rarely, if ever, started directly. Instead, it is automatically started whenever needed using a start command specified in the ODBC configuration named SOSDATA (located by default on the System DSN tab). As mentioned above, you should not simply type the encryption key in the indicated field on the Database tab because it will appear in clear text in the Windows Registry. Instead, follow the instructions in the section above to create an OPTION2.PRM file that contains an encrypted version of the database encryption option and your key. (It does no harm to make the same modifications on a network database server, but in almost all cases the database server will be started from a shortcut, batch file, scheduled task command, or as a service. The only time the ODBC configuration would be used is if you were to use the SOS Login shortcut when the database was not already running.)
You must then modify the ODBC configuration, specifically the Database tab entries as follows, assuming default SOS folders and a standalone installation:
| Configuration |
Setting |
|---|
| Server name |
SOSDATA |
| Start line (typed all on one line) |
c:\sos\sa\bin64\dbeng11.exe @c:\sos\server.prm c:\sos\data\sosdata.db @option2.prm |
| Database name |
SOSDATA |
| Database file |
<leave this field empty> |
| Encryption key |
<leave this field empty> |
| Start database automatically |
checked |
| Stop database after last disconnect |
checked |
Running an Encrypted Database as a Windows Service
If prompting for a password on startup (the -ep parameter), be sure to use the -i parameter when creating your service so the service can interact with the console. As the service starts, a window will appear in which you must type the encryption key.
The following example (typed all on one line) creates a service that prompts for the encryption key whenever you start the database:
c:\sos\sa\bin64\dbsvc -as -t network -s Automatic -i -w mysos c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db -ep
You must include the -i (allow service to interact with the desktop) option when you use the -ep (prompt for encryption key) option. When configured in this fashion, someone must be present at the server console to type the encryption key when the service starts.
Although this option would be the most secure, it may well not be practical. The alternative would be to pass the encryption key value on the service startup line automatically. The problem is that if you type the encryption key in your startup command, it is not secure. To avoid having this value exposed, the -ek parameter, along with the encryption key, may itself be encrypted in a form that the database engine will be able to decrypt. When you rebuild the database the utility will create the appropriate, ready-to-use, encrypted key parameter in a file called option2.prm.
You can also create that file manually as follows:
- Create a plain text file using Notepad or another text editor.
- Enter -ek and the encryption key with which your database was encrypted.
- Save the file as TEMP.TMP in your SOS folder.
- Now encrypt the file, saving the encrypted copy as OPTION2.PRM with the command:
c:\sos\asa\win32\dbfhide temp.tmp option2.prm
- You will now have the original TEMP.TMP and the encrypted OPTION2.PRM in your SOS folder. Once you are sure that the encryption key value is safely recorded in case you should ever need it (SOS recommends that you call SOS and have the value stored in your account records at SOS), delete the TEMP.TMP file. Hold down the shift key while deleting to be sure the file is deleted instead of simply moved to the recycle folder. If you have a utility for secure deletion of files, that would be even better.
- Now create your service using the following format (typed all on one line, with the appropriate changes if your installation is not in C:\SOS):
c:\sos\sa\bin64\dbsvc -as -t network -s Automatic -i -w mysos c:\sos\sa\bin64\dbsrv11.exe @c:\sos\server.prm c:\sos\data\sosdata.db @c:\sos\option2.prm
Note: For additional information and description of all available command line options for service creation, see: Running the SOS SQL Anywhere 11 Database as a Windows Service
Transport Layer Encryption
In addition to encryption of the database itself, a customer might be concerned about protecting the data while it is “in motion” between the server and the client workstations. Various network protection approaches are available, including VPN, wireless encryption, and use of Windows Terminal Services or Citrix.
As with database file encryption discussed previously, there are simple and strong encryption options available for transport-layer security. An easy way to avoid sending easily read data is to add…
-ec simple
…to your server startup options in the SERVER.PRM file in your SOS folder. Doing so forces all connected clients to use simple encryption on database network communications. Doing so provides the same kind of obfuscation for your database communication packets that simple encryption does for your database files. It will not secure the data from an encryption expert or “hacker” who is determined to eavesdrop on your communications, but it will prevent less sophisticated individuals from reading the contents of your transmission packets by simply hooking up a packet sniffer tool. This sort of simple encryption has a minimal impact on performance, and could be used as an extra layer of protection when using other less-than-ideal encryption, such as standard wifi WPA encryption.
Sophisticated, strong, transport-layer encryption options for your database communications are also available, using RSA or ECC certificates. As stated previously, if you want that level of protection, you should probably investigate strategies that will protect all your network communications, not just database packets. In addition, this kind of database-specific encryption requires purchase of an additional component, which is priced by number of user connections.
Coordination of Benefits (COB) among multiple insurance carriers is a significant service you provide to some of your clients. Many of you appear to be having difficulties with claims for secondary carriers in your electronic filing with Emdeon. I will walk you through the process so you are clear about how to bill secondary claims electronically.
1. Primary Payer – Regardless of whether the initial claim was sent on paper or electronically to the Primary Payer, you must have an NEIC Payer ID entered in SOS Office Manager for that payer. To enter the NEIC Payer ID in OM, go to Lookups > Insurance Carriers and find your Primary Payer. Once you have found it, click on the pencil icon to make a change and then go to the Additional Tab. Once there, find the NEIC/Payer # field and enter the appropriate NEIC Payer ID. If you do not have one entered, the Claim Adjustment Reasons (CARs) will not appear on the electronic secondary claim. (Look on the Emdeon Payer List to get the payer ID. www.emdeon.com > Payer Lists > Medical/Hospital/Dental Payers) If the Primary Payer is not on the list enter SPRNT.

2. Secondary Payer – Go to Lookups > Insurance Carriers/Plans, select your Secondary Payer and click Edit > Additional tab. Check the radio button in front of ‘Amount received from other insurance’ in the section entitled ‘For HCFA amount paid (box 29)’.

3. Payment by the Primary Payer – The Primary Payer will either pay or reject your claim. If they pay, they will often diminish the payment by certain amounts called Claim Adjustments. As you enter the Primary Payer’s payment or transfer the balance from the Primary Payer to the Secondary Payer, you must also enter the Claim Adjustment Reasons (CARs) that appear on the Explanation of Benefits (EOB). When entering the payment, apply the money to the date of service; the screen below will pop up….click on the Claim Adjustment Reasons icon to enter the CARs.

NOTE: If you have to go back and enter the CARs after posting the primary payment has been completed, you can do so very easily. Go to the client’s ledger. Double-click on the date of service for which you need to enter the CARs. Once the transaction is open, double-click on the split to the primary insurance and click on the Claim Adjustment Reasons icon.

4. Detail the Claim Adjustment Reasons (CARs) – The next step is to decide what the total amount of the adjustments is and what dollar amount is accounted for by each of the individual CARs. Here is a simple rule to use to determine what the total amount of the CARs will be:
Service Fee – Primary Insurance Payment = Total CARs
Example One: Your fee for a service is $150.00; the primary insurance company paid $80.00. If you subtract $150.00 – $80.00 you are left with $70.00. All of the Claim Adjustments (CARs) for the primary payer should total $70.00.
What is accounted for in the CARs? The CARs are the reasons given by the payer for not paying your entire fee. You must enter the primary payer’s reasons and the specific adjustments or transfers so that the primary payer’s CARs can be included in the secondary claim. You will indicate if there was an adjustment made by the primary insurance for contractual reasons, if there was a patient responsibility for the service, if there was a disallowed amount, or any other reason the primary payer indicates.
To continue the example from above: The fee for the service is $150.00 and primary insurance paid $80.00. The primary insurance contractually allows only $110.00 for the service provided so they made an adjustment of $40.00. The patient had a copay of $10.00 on this service and coinsurance of $20.
Using the formula above,
FEE – PRIMARY PAYMENT = CARs
$150.00 – $80.00 = $70.00 ($40.00 + $10.00 + $20.00)
So we are now ready to enter the information in Claim Adjustment Reasons. On your EOB, you will see that each adjustment has a Group Code and a Reason Code. To enter the $40 adjustment, select the group code CO for Contractual Obligations. Then right click in the box under Reason Code and select 45 (Charges exceed your contracted/legislated fee arrangement. This change to be effective 6/1/07: Charge exceeds fee schedule). Under Amount, enter $40 and under Total Unit Paid, enter 1.

Next you will be left to account for the patient copay of $10.00 and the patient coinsurance of $20. You will enter PR as the ‘Group Code’ for Patient Responsibility. Then use Reason Code 3 (Copay amount) and $10.00. The Total Unit Paid will be 1. Enter a second line with Reason Code 2 (Coinsurance Amount), $20.00 and Total Unit Paid equal 1.

So now when you look at that screen for the Claim Adjustment Reasons you will see the following:

The claim now balances and you have accounted for the full amount of the fee.
Example Two: The fee for the service is $150.00 but the primary insurance did not pay anything because it went towards the patient’s deductible. $150.00 – $0.00 = $150 (Fee – Primary Payment = CARs), so you need to account for the full $150.00. The EOB indicates the same maximum allowable for the service as in Example One, $110.00. The EOB indicates nothing about copay. So you will enter a $40.00 fee adjustment (CO, 45) and $110 will be entered as PR, 1 (Patient Responsibility, Code 1). The total CARS will equal $150.00. Your Claim Adjustments screen will show:



5. Generating the claim – check the box ‘Remove punctuation from data’ when you generate the claims. This should be checked regardless of whether you are generating primary or secondary insurance. In OM, go to Bills/Claims > Create HCFA/CMS 1500 Claims > highlight your option for ANSI – Emdeon and then click on Create and Output New Batch.

PLEASE NOTE: Some insurance carriers may have different requirements for how you enter the CARs. If you find that your secondary claims are being rejected for any reason that you cannot understand, you must speak to the secondary carrier for more information regarding the rejection.
The following recommendations include billing and appointment data, but not clinical data from SOS Case Manager.
- Get a copy of the SOS database on your last day. The ideal would be an encrypted zip of the files in the DATA folder. If all that is available is a backup created by some kind of backup software, then you need the name of the software used to create the backup, the version of that software, and any encryption password that was used when the backup was created. If your IT guy can restore those files and make an encrypted zip of the database files, that is much, much better. If all you have is a backup that requires particular software to restore the files, you may be out of luck seven years from now if you need the data. In either case, the files MUST BE ENCRYPTED.
- In addition, we would suggest that you generate some reports, saving the output in pdf files. First, in the Scheduler, do “Appointments for a Period, Including Cancellations” for the entire range of dates through your last day. When it comes up on the screen, click the little icon in the upper left corner and export to “Adobe Acrobat (pdf)”
- Next, in OM, do “Patient Facesheet” on the Reports > Patient Reports menu. Again, do the full date range, like Jan, 1900 through your last day, all providers, and check the box to include patients with a discharge date. That’s going to be a big report, with at least one page per patient. Export the result to a pdf as explained above.
- One more that we would suggest is also on the Reports > Patient Reports menu: “Transactions History”. You will have to do one pass for active accounts and another for inactive. Set the options with the full date range and to include zero items and zero balance patients. This report will be a monster as well. If for some reason you can’t do the pdf export of the whole thing at once, then use patient ranges to do shorter reports that cover portions of the alphabet.
- Once you have generated all the pdf files, use WinZip or 7Zip to save them into ENCRYPTED zip files. If you don’t know how to do this part, then get someone who does to help.
These pdf reports will give you easy access to anything you would be likely to need, by just searching the pdf for the desired patient name, and you would not need any special software to do it.
Finally, we would suggest you use one strong password as the encryption key for all the files, and save the password in a couple of safe places that you will remember and be able to access. The files you have generated, along with the backup, should be saved on DVD’s and/or a USB flash drive. Carefully label all the media and store in your safe deposit box.
The 2013 CPT codes must be entered manually in your SOS software. SOS does not provide CPT codes nor does it update your CPT codes list. SOS 2013 does, however, provide a new feature to make adding a new entry to your list of services quick and easy.
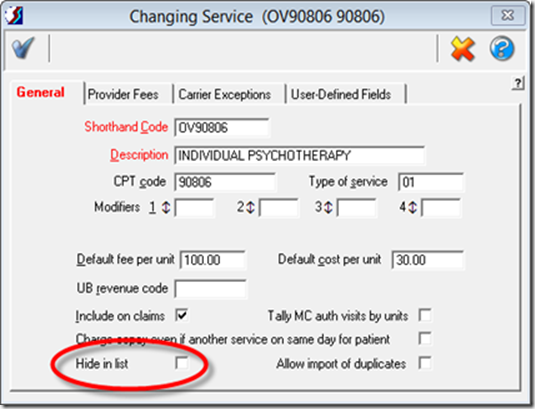
If any of the CPT codes that you use are among those changed for 2013, you must use the new CPT codes for all services rendered on January 1st, 2013 and later. if you need to file or re-file any claims prior to January 1st, 2013, however, you will have to submit them with the old codes. For that reason, you probably should retain your old codes and add new, 2013 versions of those codes. To minimize confusion, you might want to hide the old service code entries as soon as you finished entering and submitting claims for 2012 visits. To hide an item, just check the Hide in list option in the lower left corner of the Service window:
How do I enter a new service code?
If you are entering a brand new code that is not replacing one you already have, then you should enter it manually by going to Lookups > Services. and then clicking the Add (green “plus”) icon.
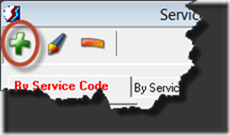
Enter the shorthand code and the description. Remember that the shorthand code and description must be unique, so you cannot use the same shorthand code or description as your old code. If you want to use that code or description for the new service item, you must first change the code and/or description in the old one. If either code or description is exactly the same as an existing entry (whether visible or hidden), an error will prevent you from saving your new entry.
If you are creating a 2013 version of an existing code, especially if the old code has several provider/provider type fees and/or carrier exceptions that you want to use on with the new code:
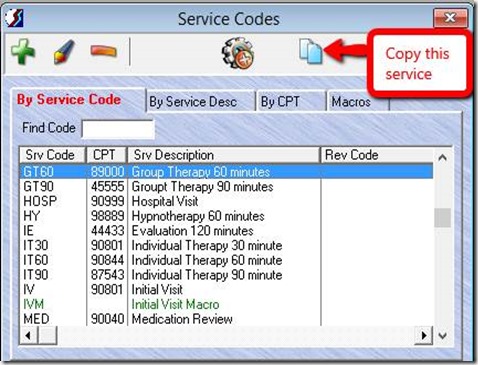
- Highlight the existing code code in the list.
- Click the “Copy” icon in the toolbar at the top of the window.
- A window will open, prompting you for a new shorthand code and description. Make sure you replace or change the old shorthand code and description
in some way.
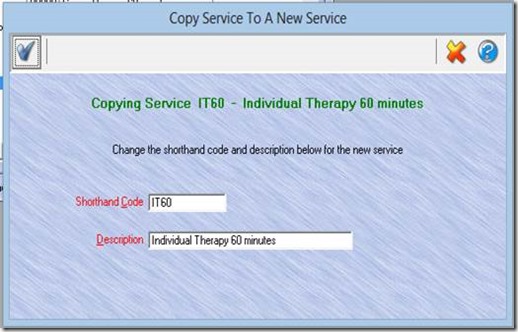
- Click on the Blue Check icon to save.
How do I enter “Add-On” codes?
Beginning in 2013, certain types of services require the addition of Add-On codes to provide insurance payors with more detailed information about the service rendered. These Add-On codes are entered as regular service codes.
For example, let’s say that you see a client for “Psychotherapy for 45 minutes with Interactive Complexity”. Prior to January 2013, you would have created a single charge entry, using the service code in your list that designates 90812 as the CPT code. After January 1st, 2013, you would use 90834, which indicates “Psychotherapy 45 minutes”, and a second charge entry for 90785 for “Interactive Complexity”. So prior to January you would have entered one charge for this client with the CPT code 90812. After January 2013 you have to enter two services: one with 90834 and one 90875. Each code has an assigned fee, make sure you verify with your payers to get that information. If you must file the additional code with a fee of zero, then you must be sure to assign the service code to a Service Category (Lookups > Service Categories). If needed, just create a new category which you can name “Zero Fee” or something of the sort, and assign your new Add-On service to that category. OM will always include “include on claims” services that are part of a Service Category on your claims, even if there is no fee for the service. For more information, see Printing Claim Detail Lines When Fee Is Zero.
The use of Add-On codes can have the unintended consequence of causing your authorization visit tallies to be incorrect. Both the main and Add-On codes will each be counted, so a single actual visit will reduce SOS’s count of remaining visits by two instead of just one. In the January 31, 2013 update a change was made to the Tally MC Auths by the option on the Service form (Lookups > Services) so that you can now select “Exclude” rather than the prior options of “Visits” and “Units”:
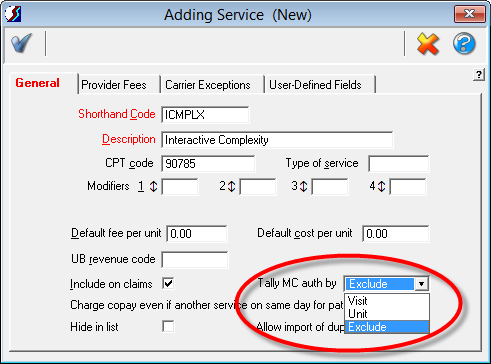
If your practice requires the use of Add-On codes like the one above, you will have to create at least two charge entries for the same date of service. In SOS, the fastest and easiest way to enter two or more related services is through the use of Service Macros.
What is a service macro and how are they entered in OM?
If some of these code combinations will be used frequently in your practice, you will want to use an SOS service macro to make your data entry faster. A service macro is used like a regular service code, but when you save a charge entry in which a macro code is used, SOS will expand it, creating two or more charge entries for you – one for each of the codes that the macro contains. Returning to our example above, we want to enter both a 90834 and a 90735 to describe the service that was rendered, so we will first create a macro that contains both of those service codes.
To enter a Macro:
- Go to Lookups > Services > Add a Macro(the gear with plus sign icon).
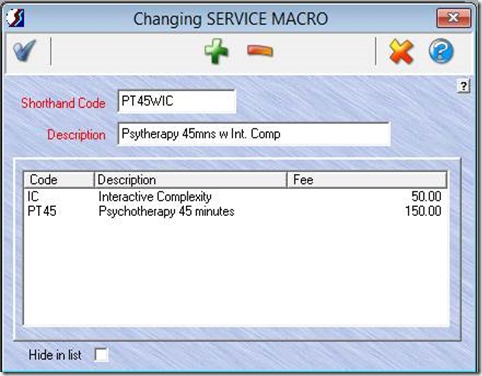
- Once you click Add a Macro, a window will open. Enter a shorthand code and a description, such as “Psychotherapy 45 minutes and Interactive Complexity”.
- Next, click ADD (green “plus” icon) to attach the two service codes that will make up this macro, . Once the two codes are entered it will look like the screen below.
- Click Save (blue “check” icon).
Create macros for all the different code combinations that you will be using. Macros will appear in green in your service code list. You can maintain (change or delete) your macros on click the Macro tab of Lookups > Services.
How do I enter a macro charge in the daysheet?
Still using our example, let’s use our new macro to enter a charge in the daysheet. Start your new charge entry normally, completing all fields as you usually do, except for the Service field. For Service select your new macro from the Services lookup list instead of an individual service code. (If you import your appointments from the Appointment Scheduler or from Case Manager, use the macro code for the service when you enter appointments or progress notes.) Additionally, you cannot enter a fee as you normally do. The screen will show the total of the default fees specified in each service contained in the macro. You will have an opportunity to make changes in the next step. Make sure that you have a value in each of the required (red) fields. You will notice that you will not see any splits in the lower part of the window as you usually do.

When you click Save (blue “check” icon) on the main charge entry screen, a “Changing MACRO” window will appear, showing the way the macro will be expanded, with one line for each daysheet entry it will create. If you want to change the provider, fee, units, or other values for any of these about-to-be-created charges, this is your opportunity to do so. Just double-click the item you want to change (or highlight the item and click the Change icon (“pencil”) in the toolbar. When you have completed any desired changes, proceed by clicking Save (the “check” icon).
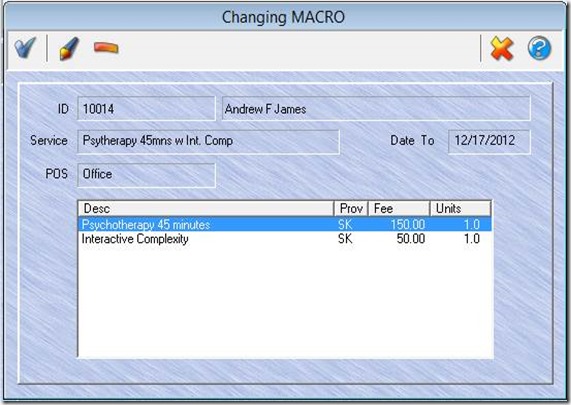
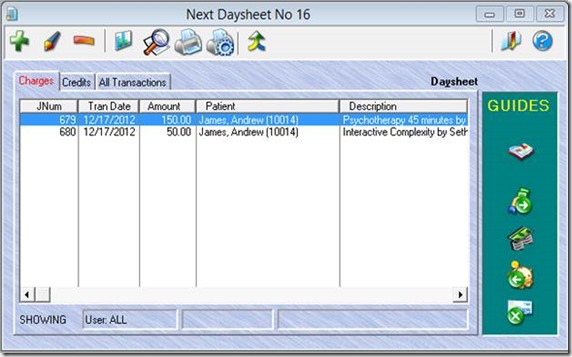
Below you can see the result: one charge for 90834 and another for 90735.
On a stock Window Vista, Windows 7 or Windows 8 computer, attempts to access the built-in help system in SOS modules will result in an error message, stating that your current version of Windows does not support the program’s help system. The needed help system software is available on the Microsoft Downloads site, from which you can download and install the missing component.
The following page on the web contains links to the correct WinHlp32 installer for all of the current versions of Windows, including Vista, Windows 7, and Windows 8:
http://www.microsoft.com/en-us/download/search.aspx?q=WinHlp32.exe
|
|

 Print Friendly
Print Friendly








